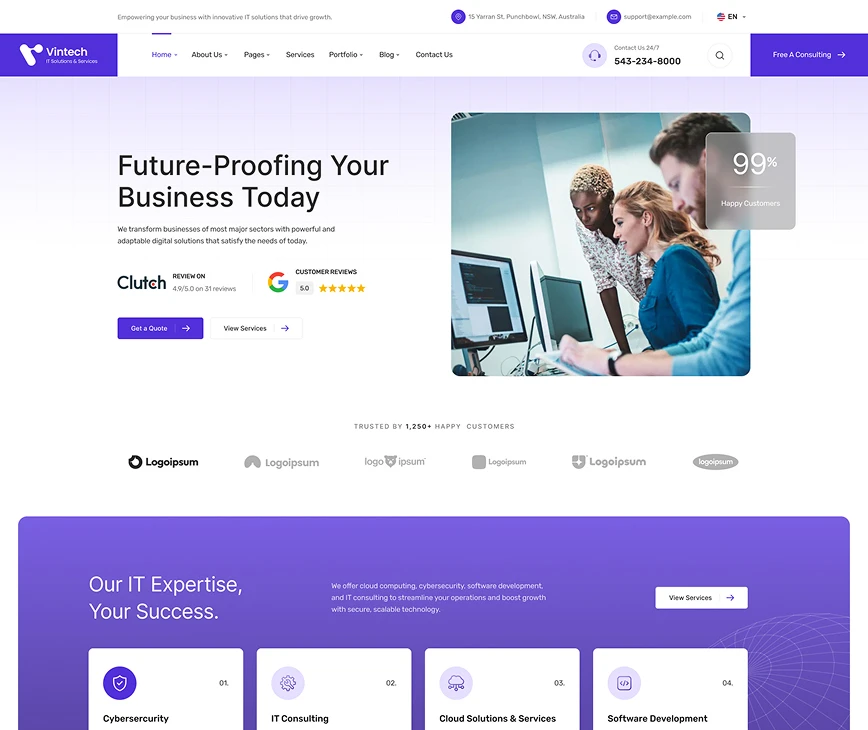
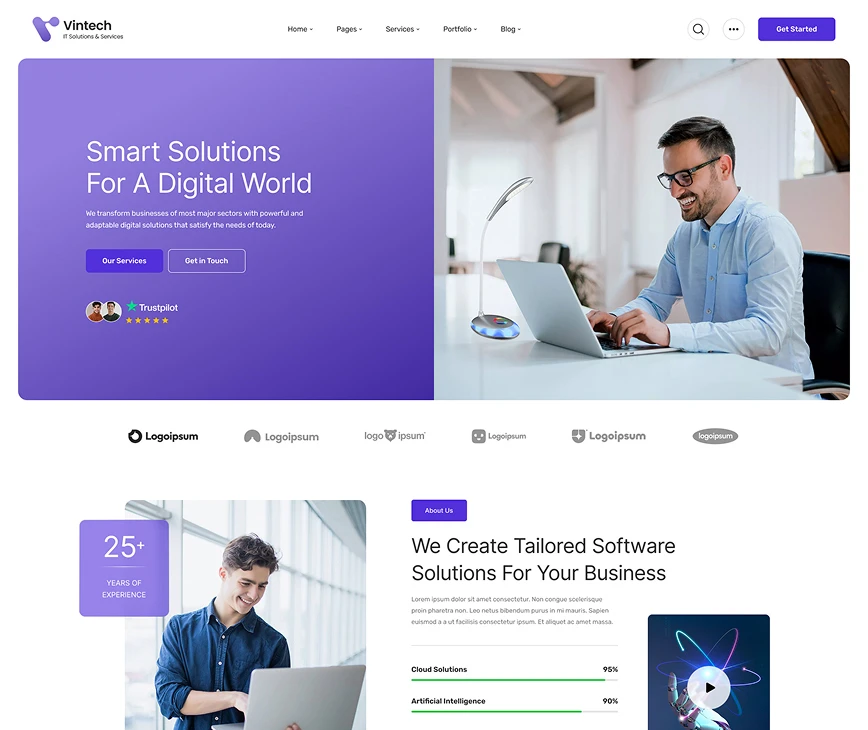
Future-Proofing Your Business Today
We transform businesses of most major sectors with powerful and adaptable digital solutions that satisfy the needs of today.

REVIEW ON
cUSTOMER REVIEWS

Our IT Expertise, Your Success.
We offer cloud computing, cybersecurity, software development, and IT consulting to streamline your operations and boost growth with secure, scalable technology.
Security Risk Assessment
Customized Security Trainings
Security Audits & Compliance
Security Management
Policy Development
Research & Development
IN IT SOLUTION
Your Challenges, Our Solutions – IT Done Right, With Precision and Care
With more than 25 years of proven expertise in the IT industry, we have built a strong reputation for delivering innovative and reliable technology solutions that empower businesses to grow and thrive in an ever-evolving digital landscape. Our journey has been defined by a commitment to excellence.
Our mission is to be a trusted technology partner that enables businesses to reach their full potential through smart and scalable IT solutions.
We believe in leveraging the power of innovation to simplify complexity, enhance performance, and drive real business outcomes.
From Vision to Victory,
Turning Ideas Into Reality
At Vintech, we embrace continuous improvement as our foundation. Every day, we refine our skills and push for excellence in everything we do.
Empathy
We prioritize understanding and compassion, ensuring that our solutions resonate with the unique needs of our clients.
Performance Driven
We are committed to delivering high-quality results, continuously optimizing performance to exceed expectations.
Our Case Studies
Our IT solutions empower businesses with innovative ideas and excellent service.
Creative Team in Strategy Session
Creative Team in Strategy Session
How We Deliver Innovation and Excellence
1
Understand Your Needs
We begin every project by carefully understanding your unique business goals, challenges, and audience. This deep discovery process ensures we create a solution that’s not only relevant but also built around your specific needs and expectations.
2
Design Tailored Solutions
Our team transforms insights into strategic, creative, and scalable solutions. Every element is customized to align with your vision, ensuring the final product is both impactful and functional—designed to solve real problems and deliver measurable results.
3
Deliver And Support
We focus on delivering high-quality, on-time results with a seamless process. Post-launch, we remain committed through ongoing support, improvements, and optimization—ensuring your investment continues to perform and adapt to evolving business needs.
Our Pricing Plan
Basic Plan
Perfect for growing businesses with moderate IT needs
Features
Business Plan
Perfect for growing businesses with moderate IT needs
Features
Enterprise Plan
Perfect for growing businesses with moderate IT needs
Features
Basic Plan
Perfect for growing businesses with moderate IT needs
Features
Business Plan
Perfect for growing businesses with moderate IT needs
Features
Enterprise Plan
Perfect for growing businesses with moderate IT needs
Features
Your Questions, Answered – Clarity Starts Here.
Lorem ipsum dolor sit amet consectetur. Hendrerit quis adipiscing suspendisse feugiat ut ut pellentesque.
Empowering Innovation, Leading with Expertise.
Lorem ipsum dolor sit amet consectetur. Hendrerit quis adipiscing suspendisse feugiat ut ut pellentesque.
What Your Future Co-Workers Say?
We blend cutting-edge technology with eco-friendly practices to build structures that stand the test of time. Our commitment to quality, efficiency, and sustainability ensures every project is built for the future.

Peter Parker

Michael Carter

Daniel Vaughn

Sophia Reynolds
Latest insights and updates on technology trends and innovations
Security Audits & Compliance — Your Shield Against Costly Penalties and Cyber Threats
Why Every Business Needs a Cybersecurity Risk Assessment—Before It’s Too Late
The Human Firewall — Why Employee Training is Your First Line of Cyber Defense
Ready To Transform Your Business? Book a Free Consultation
Leave your email below to start a new project journey with us. Let’s shape the future of your business together.
 EN
EN